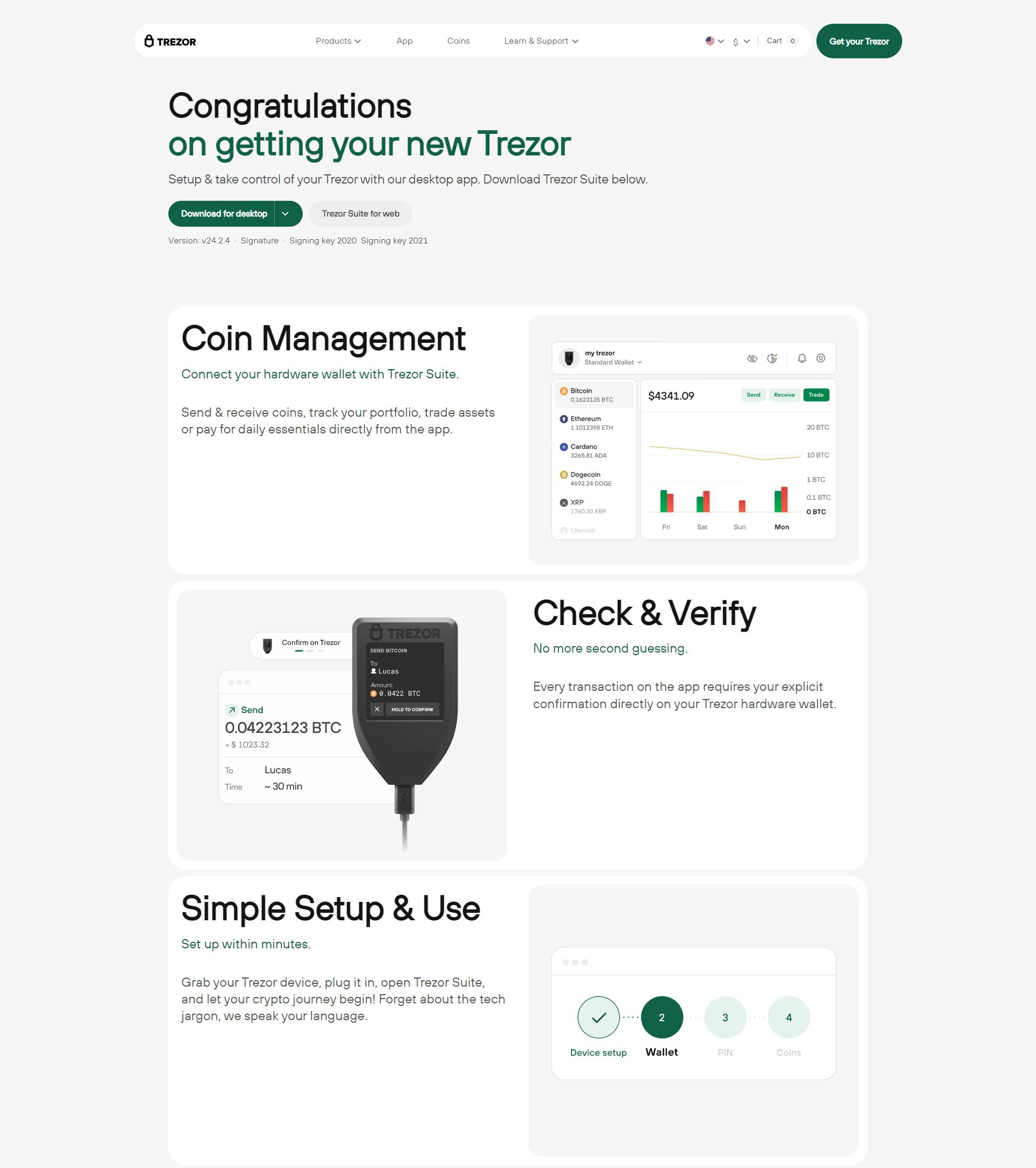
Trezor: The Safest Way to Protect Your Digital Assets
The world of cryptocurrency is exhilarating, but it also comes with significant risks. Digital assets are often targeted by hackers and fraudsters, making security a top concern for anyone involved in crypto. This is where Trezor comes in. Trezor, a highly regarded hardware wallet, is designed to protect your private keys offline and offers a safe and easy way to manage your crypto portfolio. In this article, we’ll walk you through everything you need to know to get started with Trezor, from setup to advanced usage.
What Is Trezor?
Trezor is a hardware wallet that allows you to securely store cryptocurrencies such as Bitcoin, Ethereum, and Litecoin offline. By keeping your private keys offline, it shields your funds from online hacks and malware that could affect software wallets or exchanges. Trezor was the first hardware wallet to market and has become a trusted name in the cryptocurrency community for its robust security features and ease of use.
Key Benefits of Using Trezor
- Offline Security: Trezor stores your private keys offline, making it immune to online attacks like phishing and hacking.
- Multi-Currency Support: Trezor supports a wide range of cryptocurrencies, including Bitcoin, Ethereum, Litecoin, and over 1,000 others.
- User-Friendly Interface: Even for beginners, the Trezor setup and interface are intuitive, ensuring that anyone can secure their funds with ease.
- Recovery Options: Trezor provides a recovery seed that allows you to recover your wallet if the device is lost or damaged.
- Advanced Security Features: Features like PIN protection, passphrases, and two-factor authentication add an extra layer of protection to your wallet.
How to Set Up Your Trezor Wallet
Setting up your Trezor device is simple and straightforward. Follow these six easy steps to get started:
Step 1: Unbox and Check the Contents
Upon opening your Trezor box, you should find the device, a USB cable, and a recovery seed card. The recovery seed is critical—it’s your backup in case anything happens to your Trezor device. Make sure to write it down and store it in a secure place.
Step 2: Connect Your Trezor to a Computer
Use the provided USB cable to connect your Trezor wallet to your computer. Once connected, the Trezor device will prompt you to visit the Trezor website to begin the setup process.
Step 3: Install Trezor Bridge
To allow your Trezor device to communicate with your computer, you’ll need to install Trezor Bridge. This software facilitates secure interaction between the device and your web browser. Download it from the Trezor website and follow the installation prompts.
Step 4: Set Your PIN
For added security, Trezor will ask you to create a PIN code. This PIN is required each time you access your wallet, providing an extra layer of protection. Choose a PIN that is easy for you to remember but difficult for others to guess.
Step 5: Record Your Recovery Seed
Trezor will generate a 12 or 24-word recovery seed that is essential for restoring your wallet if you lose your device. Write down the recovery seed on the card provided and store it in a safe location. Do not store it online or share it with anyone.
Step 6: Begin Using Your Trezor Wallet
Once you’ve completed the setup, your Trezor is ready to use. You can now send, receive, and manage your cryptocurrencies securely. If you want to use additional features or coins, simply install the relevant apps from the Trezor wallet interface.
Frequently Asked Questions (FAQs)
What happens if I lose my Trezor device?
If you lose your Trezor device, you can still recover your wallet using the recovery seed. As long as you have the seed phrase, you can restore your wallet on another Trezor device or a compatible wallet.
Can I use Trezor with my mobile device?
Yes, Trezor is compatible with mobile devices. By using a USB OTG cable, you can connect your Trezor device to your smartphone and access your wallet through supported apps.
Is Trezor safe from hackers?
Yes, Trezor offers excellent security. Because it stores your private keys offline, it is immune to online threats such as phishing and malware that affect software wallets.
Conclusion: Your Crypto, Safely Stored with Trezor
Trezor provides one of the best solutions for securing your cryptocurrency. By following the steps outlined in this guide, you can protect your assets from online threats while enjoying easy access to your funds. Start securing your digital wealth with Trezor today.